Static code analysis – a developer’s best friend
With computer hackings and cyber attacks rising exponentially worldwide, organizations are struggling to clearly define their security strategies. Applications are becoming more and more advanced with their functionality, but they are also allowing hackers to access sensitive user information (data theft) or even carry out Denial of Service (DoS) attacks.
Static Code Analysis – A Developer’s Best Friend http://t.co/X0h9WSCvxn pic.twitter.com/XZwljU9Mho
— Sticky Password (@stickypassword) October 19, 2015
Organizations are constantly failing to protect applications and their backend servers – the hacker’s ultimate goal. Customer data security has to be prioritized, but this goal is obviously not being achieved. The Ashley Madison fiasco is just one example of a recent mega-hacking where sensitive customer data was stolen and even publicly exposed.
Traditional Solutions Are Not Getting the Job Done
Security executives have long relied on three traditional security solutions to safeguard their applications. Penetration (Pen) Testing, the Web Application Firewall (WAF) and Dynamic Application Security Testing (DAST) have been extensively used by organizations, but the effectiveness of these old solutions is constantly declining.
Pen Testing – Arguably the oldest application security solution, Pen Testing is effective in mimicking the hacker’s actions and finding crucial flaws, but multiple cycles of testing have to be performed to reach optimal results. This makes it a very costly process, in addition to the fact that it enters the frame only after the applications is up and running.
WAF – This tool is very popular for monitoring web traffic and blocking attacks in real time, but it also requires very accurate configurations that have to be tweaked every time the code is changed. False Positives (FP) are a common problem with these types of firewalls. That’s why organizations rarely set WAFs to block traffic.
It should also be mentioned that maintaining a WAF solution requires extra resources to filter out false positives and tweak the solution for optimal results.
DAST – Also known as Black Box Testing, DAST is being used extensively by organizations worldwide. It involves the sending of requests and analyzing the responses received by the application. Unfortunately, DAST can be used only after a complete build is reached, leading to ROI issues just like with Pen Testing.
Also, due to its inherent deficiencies, DAST can detect only reflective flaws. This leaves out many major non-reflective flaws such as the infamous Cross-Site Scripting (XSS).
The Top 5 Benefits of Using Static Code Analysis (SCA)
Static Code Analysis (SCA) is basically the automating of the security process to create a secure Software Development Life Cycle (sSDLC). These code scanners sit within developer IDEs as light-weight plugins and provide almost real-time results with in-depth analysis of the application code for quick detection and remediation.
1 – Return on Investment (ROI)
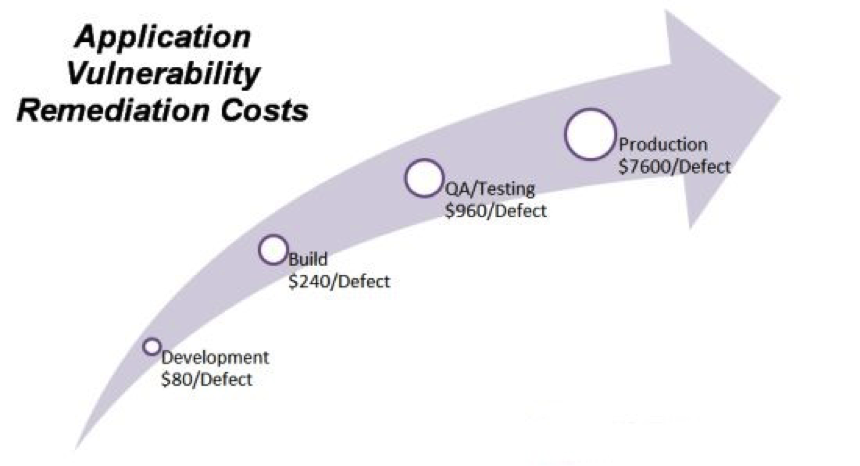
Static Code Analysis can be initiated in the coding stage. Some solutions even allow raw chunks of source code to be thrown at the scanner to start locating application layer vulnerabilities. The implementation of security in the development stage has significant financial advantages, as evident in the Ponemon Institute infographic below.
Vulnerabilities detected during development stage are significantly cheaper to tackle compared to flaws detected in the latter stages of the development life cycle.
2 – Fast Installation and Wide Coverage
Static Code Analysis (SCA) solutions are typically out-of-the-box products that can be installed and configured easily. Also, scanning source code allows for the early detection of a wide range of vulnerabilities and coding errors. These include all the top security issues mentioned in popular reference lists such as the OWASP Top 10 and SANS 25.
3 – Great for Agile and DevOps Scenarios
As mentioned earlier in the article, the automating of the security process and almost real-time scanning makes SCA a good choice for organizations using Agile or DevOps development methodologies. With Static Code Analysis, the application code can be scanned with each commit, enabling quick detection and mitigation of flaws.
4 – Promotes Application Security Awareness among Developers
Leading SCA solutions have comprehensive vulnerability reporting provisions. This in-depth analysis can be broken down as per the organization’s requirements and can even be exported for offline scrutiny. This helps keep the developers involved in the security process and eventually helps boost their secure coding awareness.
5 – Doubles as a QA Solution
QA has become an integral part of the modern development process. The problem is that its late entry into the process can lead to delays in the product release or in many cases force the organization to release buggy applications. SCA helps detect coding flaws such as dead code and logic errors very early in the SDLC, eliminating such issues.
The Bottom Line
Source Code Analysis, which is basically a Static Application Security Testing (SAST) methodology, is proving to be an efficient way to secure application code.
“SAST should be a mandatory requirement for all IT organizations that develop or procure applications.” American IT research and advisory firm Gartner says about web and mobile application security. “Ideally, application vulnerability detection would be conducted continuously during the entire software life cycle (SLC).”
But despite all the advantages and endorsements, Static Code Analysis (SCA) is not a silver bullet when it comes to developing robust applications with high code integrity.
Organizations are best advised to combine two or more security solutions to locate as many vulnerabilities as possible in the application code before it is released to the market. This reduces the need for costly post-release patches and updates, not to mention the minimization of financial damages caused by potential security breaches.
For example, using Static Code Analysis (SCA) during the application development process and complimenting it with a few cycles of Pen Testing prior to release can be an effective way to safeguard the application inside-out. Only a proactive multi-layered approach can minimize vulnerabilities and ensure a secure product life-cycle.
Application security is no longer a choice. Stay safe!
About the author
To learn more about Static Code Analysis and Static Application Security Testing (SAST) please visit, www.checkmarx.com.