Comment gérer vos appareils de confiance dans votre StickyAccount
Sticky Password vous offre la sécurité la plus efficace du marché, mais l’optimise également en vous permettant de définir les appareils que vous utilisez avec StickyAccount, à savoir les appareils autorisés à utiliser votre licence, à accéder à vos données et à se synchroniser avec vos autres appareils de confiance.
Qu’est-ce qu'un appareil de confiance ?
Les appareils de confiance sont les appareils autorisés à être utilisés avec votre Sticky Password, ainsi que les navigateurs autorisés à se connecter à votre StickyAccount sur le site my.stickypassword.com.
Pour pouvoir utiliser Sticky Password, chaque utilisateur doit créer un compte utilisateur unique appelé StickyAccount. La création du StickyAccount a lieu lors de la première installation de Sticky Password sur l’un de vos appareils. L’assistant Première exécution, qui fait partie du processus d'installation, vous aide à définir les paramètres nécessaires et à tout configurer. Ce n’est qu’après sa création que vous pouvez accéder à votre StickyAccount pour gérer vos paramètres via le site Web my.stickypassword.com.
Un appareil de confiance est un appareil que vous avez autorisé à (plus d'informations sur l’autorisation d'un appareil ci-après) :
se connecter à votre StickyAccount personnel ;
utiliser les fonctions activées par votre clé de licence Sticky Password ;
télécharger ou synchroniser votre base de données chiffrée avec vos données (synchronisation et sauvegarde disponibles avec les licences Premium).
Un appareil de confiance peut être ::
votre ordinateur de bureau, ordinateur portable, téléphone mobile ou tablette sur lesquels vous avez installé Sticky Password ;
un navigateur que vous utilisez pour vous connecter à votre StickyAccount via notre interface Web sur my.stickypassword.com.
Gestion des autorisations des appareils : ajouter des appareils de confiance à votre compte
Ce paramètre permet de définir la manière dont les nouveaux appareils, ceux ajoutés à votre liste d’appareils de confiance, peuvent se connecter à votre StickyAccount, notamment, par exemple, lorsque vous installez Sticky Password sur un nouveau téléphone (il est nécessaire de connecter chaque nouvelle installation à votre StickyAccount) ou la première fois que vous voulez vous connecter via un nouveau navigateur à votre StickyAccount sur notre site Web.
Connectez-vous à my.stickypassword.com.
Accédez à l’onglet Paramètres - Section Autorisation.
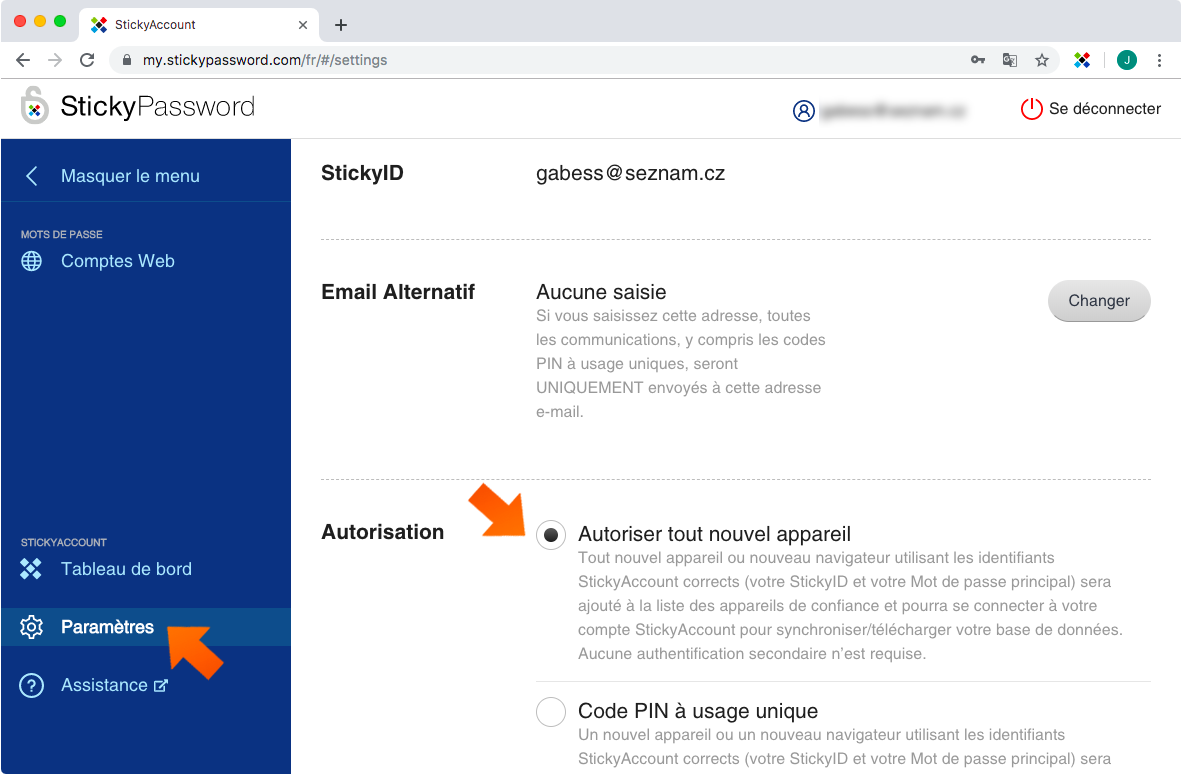
3. Vous disposez de trois options :
Autoriser un appareil (paramètre par défaut)
Un appareil/navigateur disposant des informations d'identification StickyAccount correctes (votre StickyID et votre mot de passe principal) peut synchroniser la base de données et accéder à votre StickyAccount. Aucune authentification secondaire n’est nécessaire pour connecter un nouvel appareil à votre StickyAccount.
Code PIN à usage unique (paramètre recommandé)
Un code PIN à usage unique est envoyé à votre adresse StickyID ou adresse e-mail alternative (si elle est définie) et doit être entrée après vos informations d'identification StickyAccount (votre StickyID et votre mot de passe principal). Une fois le code PIN entré, l’appareil est ajouté à la liste des appareils de confiance.
Pas de nouvel appareil
Aucun nouvel appareil (un appareil qui ne figure pas dans la liste des appareils de confiance) n’est autorisé à se connecter à votre StickyAccount. Aucun appareil ne figurant pas dans la liste des appareils de confiance n’est autorisé à se connecter à votre StickyAccount. Pour ajouter un nouvel appareil, vous devez remplacer préalablement ce paramètre par l’un des paramètres ci-dessus. Après avoir ajouté l’appareil, veillez à réactiver le paramètre Aucun nouvel appareil.
Remarque : À des fins de sécurité, il est recommandé d'utiliser la deuxième option Code PIN à usage unique. C’est un moyen simple de renforcer votre sécurité personnelle.
Gestion des appareils de confiance
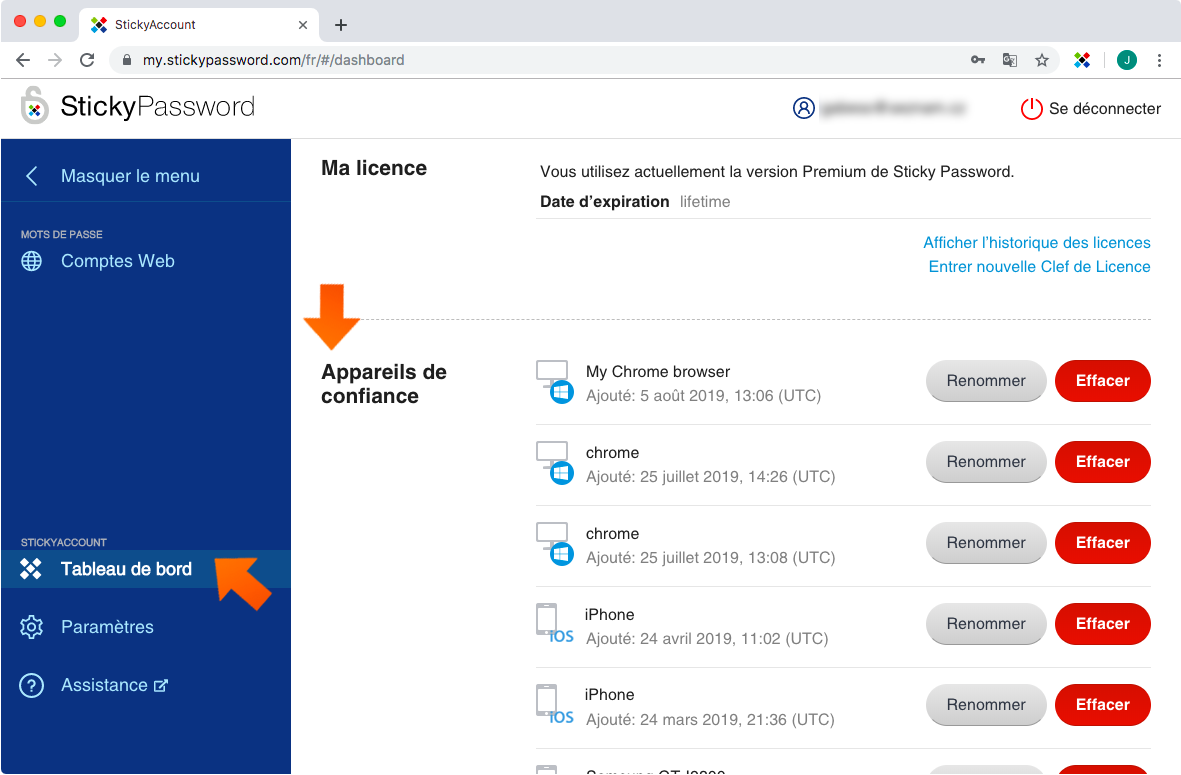
Il est judicieux de vérifier de temps à autre la liste des appareils de confiance. Utilisez-vous toujours tous les appareils de la liste ? Supprimez les appareils que vous n’utilisez plus. Lorsque vous supprimez un appareil de la liste, ce dernier ne peut plus se connecter à votre StickyAccount, utiliser les fonctions activées par votre clé de licence et télécharger et synchroniser vos données.
Connectez-vous à my.stickypassword.com. Cliquez sur Tableau de bord et défilez vers le bas jusqu’à la section Appareils de confiance. Elle contient la liste des appareils de confiance. Vous pouvez identifier tous les appareils que vous utilisez (ou avez utilisés par le passé) avec Sticky Password, ainsi que les navigateurs que vous utilisez (ou avez utilisés) pour accéder à StickyAccount.
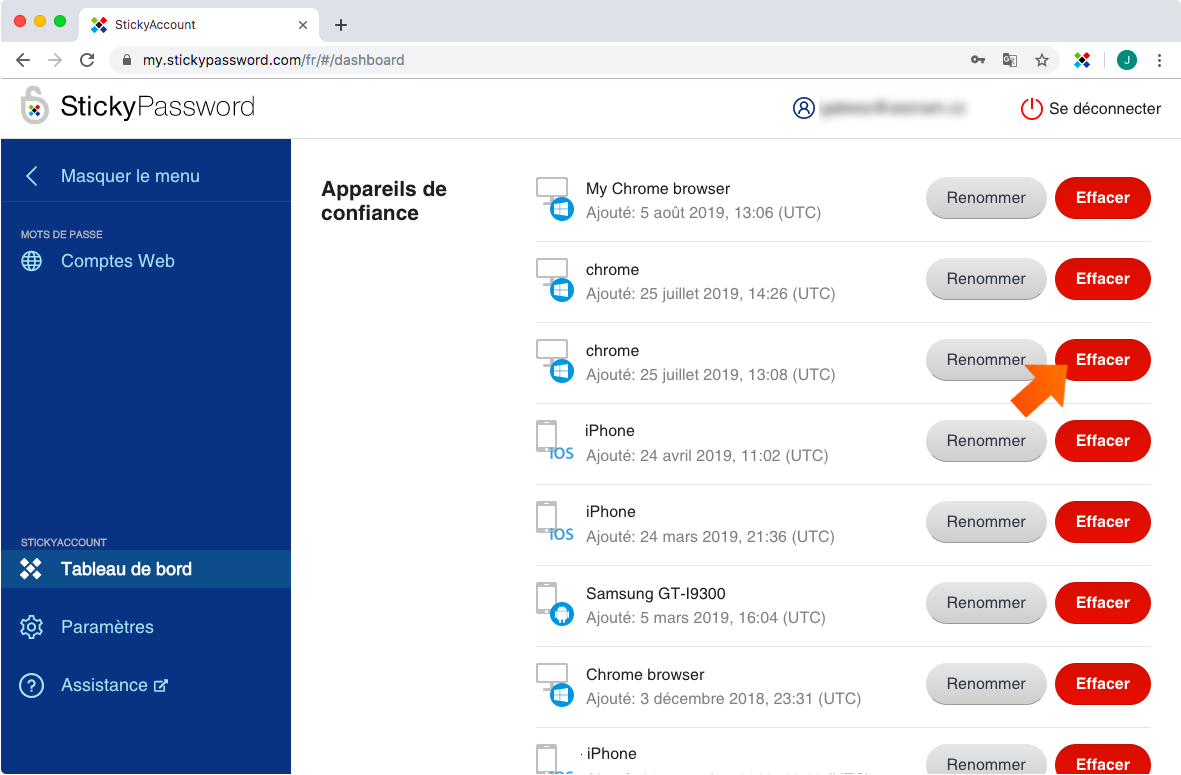
Pour supprimer un appareil, cliquez sur Effacer.
Confirmez l’opération en cliquant sur Effacer.
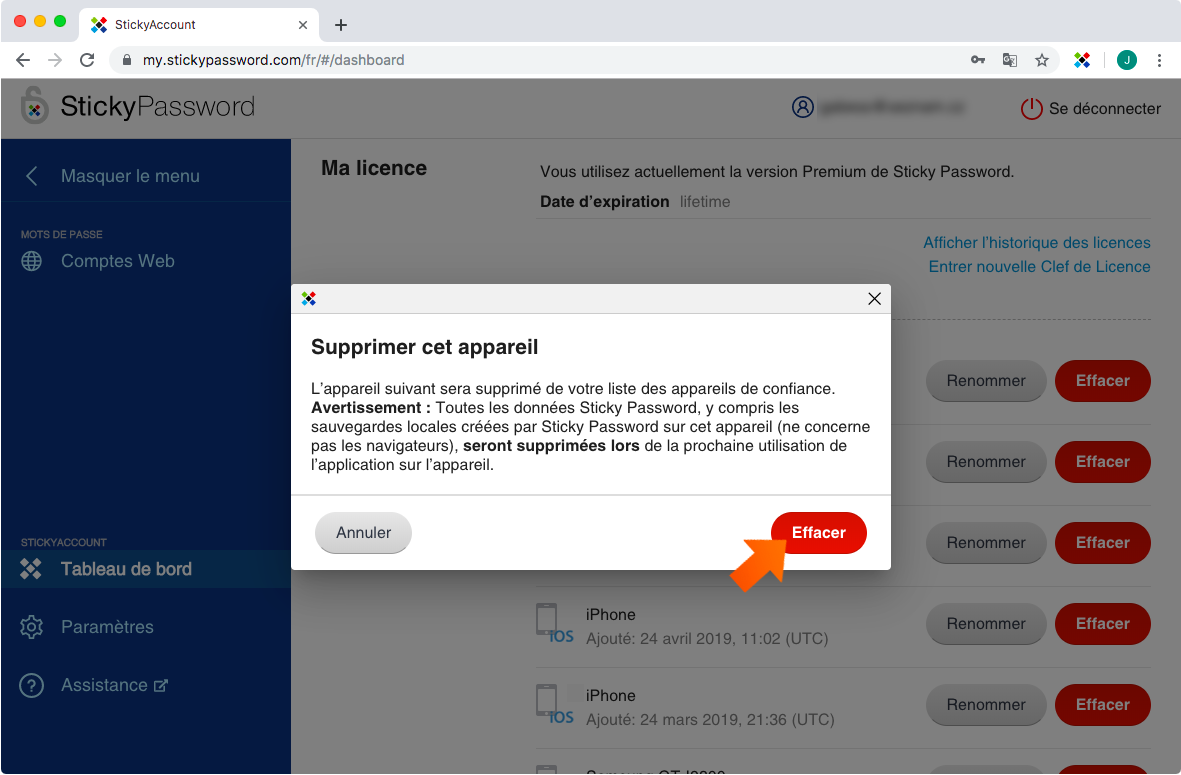
Remarque importante :Toutes les données Sticky Password, y compris les sauvegardes locales créées par Sticky Password sur ce périphérique (cela n’inclut pas les navigateurs) seront supprimées lors de la prochaine utilisation de l’application sur cet appareil.
Comment pourrions-nous améliorer notre réponse ?
Envoyer un commentaireMerci !
Merci ! Nous ferons de notre mieux pour améliorer cette réponse.
Une erreur s'est produite. Nous nous excusons pour les inconvénients. Veuillez réessayer.
