How your automatic autofill settings protect you against XSS attacks
Sticky Password is designed to detect hidden forms, thereby protecting you from a common technique used in Cross-Site Scripting (XSS) attacks. For added protection against this new pernicious attack, the default setting of the automatic autofill feature is “off”. This is additional security measure to protect your sensitive data.
In XSS attacks, an attacker can inject malicious code into a legitimate website you visit. If automatic autofill were enabled, it could fill in your details into a hidden form created by this malicious code, unknowingly sending your data to the attacker. Our password manager is equipped to detect such hidden forms, but bad actors continue evolving new hacking techniques. Sticky Password along with our counterparts in the authentication/password manger industry are dedicated to ensure that attackers cannot bypass detection systems.
When using Sticky Password autofill, click on the login or password field on the web page and Sticky Password will display a popup where you can select the appropriate login. This popup is an additional strong layer of protection because it can’t be accessed by a hackers script running on the webpage.
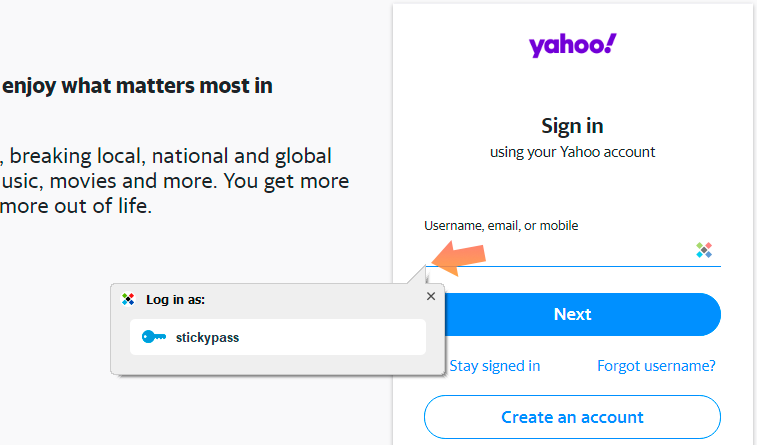
We understand that this is a change from what you were used to, but because the safety of your data is of paramount concern, we recommend applying the new setting.
While we have disabled automatic autofill by default, we understand that some users may still wish to enable this feature. To manually enable automatic autofill for all your accounts, follow these steps:
- Open the application and navigate to the Settings (Preferences) window.
- From there, select the "General" section.
- Look for the option "Enable autofill for all accounts" and click on the checkbox to enable it.
Please note, enabling this option will allow autofill to fill in your details without requiring your explicit confirmation. This can potentially expose you to risks such as Cross-Site Scripting (XSS) attacks. We recommend being mindful of the websites you visit and using this feature cautiously.
